By Raheel Ahmad
Backtracking Kali Linux will end up in the last release of Backtrack Linux. Kali the new presentation of Backtrack Linux, the security distribution to perform security auditing and penetration testing and computer forensic analysis.

Figure 1. Kali Linux
UNIX was not designed to stop its users from doing stupid things, as that would also stop them from doing clever things. (Anonymous Quotes)
The developers of Kali Linux say If you are looking for a Linux distribution to learn the basics of Linux and need a good starting point, Kali Linux is not the ideal distribution for you. You may want to begin with Ubuntu or Debian instead (Kali Linux Official website).
Highlights of Key Features of Kali Linux
Complete rebuild of backtrack Linux distribution with fully customizable and more than 300 penetration testing tools. Easy upgrading and updating and most importantly it gives you the forensic mode while booting up Kali Linux.
Forensic Mode
A quite useful feature if you want to perform some real world forensic work around. Again if you backtrack this feature you will find that Backtrack Linux introduced the forensic boot option but it has now strengthened a bit.
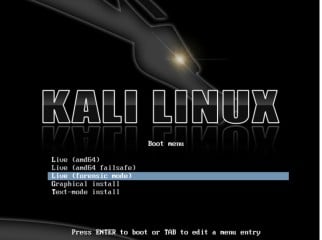
Figure 2. When booted into the forensic boot mode, there are a few very important changes that are made
“First off, the internal hard disk is not touched. This means that if there is a swap partition it will not be used and no internal disk will be auto mounted. To verify this, we took a standard system and removed the hard drive.
Attaching this to a commercial forensic package we took a hash of the drive. We then re-attached the drive to the computer and booted up off of Kali in forensic boot mode. After using Kali for a period of time, we then shut the system down, removed the hard drive, and took the hash again. These hashes matched, indicating that at no point was anything changed on the drive at all.
The other, just as important, change that was made was we disabled the auto mount of any removable media. So thumb drives, CDs, and so on will not be auto-mounted when inserted. The idea behind all of this is simple: Nothing should happen to any media without direct user action. Anything that you do as a user is on you.” [Kali Linux]
Why Kali Linux
It is hard to answer why you must use Kali Linux and not any other security distribution for performing penetration testing and network security auditing. However you don’t have much choice here other than customizing one for your own use and that’s what core security experts do.
A small history of Kali Linux would be outlined Kali as offshoot of Backtrack, which is an offshoot of [WHAX] which is itself an outcome of [WHOPPIX] which was derived from [KNOPPIX] something really in common among these names.
“UNIX was not designed to stop its users from doing stupid things, as that would also stop them from doing clever things. (Anonymous Quotes)” So, you should use Kali Linux yourself to get most out of it.
Figure 3. Time to enter the lab environment
Key is the question of where do new ideas come from. Historically, four places: government labs, big corporations, startup companies, and research universities. Now its time for you to get most out of Kali Linux!
Figure 4. Signing into Kali Linux
Authentication
During installation, Kali Linux allows users to configure a password for the root user. However, should you decide to boot the live image instead, the i386, amd64, and ARM images are configured with the default root password – “toor“, without the quotes
Penetration Testing Environment
Kali Linux provides you security tools for each phase and step of your penetration-testing project.
To accomplish this all of these tools are clubbed together under the Kali Linux tab in the applications.
To accomplish this all of these tools are clubbed together under the Kali Linux tab in the applications.
Since Kali Linux as more than 300 tools which can be used as on need basis and security testers choice the best part is that all of these tools are organized as of there behavioral approach and for the purpose these tools written.
This gives you one box, which can act as a complete solution of your needs to perform any network security auditing and penetration testing. And you can further customize Kali Linux as of your requirements and experience on these security tools.
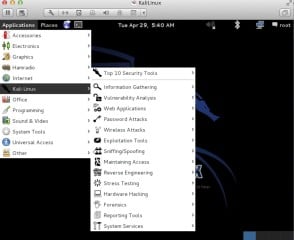
Figure 5. Moreover you can also find top 10- Security Tool separately in tabular way includes popular crackers, OWSAP-Zap, Maltego, Wireshark and last but not the least the famous Metasploit framework
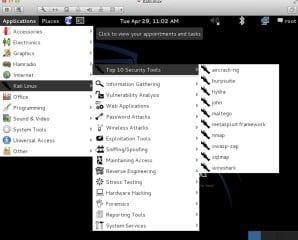
Figure 6. Penetration testing methodologies, which are most famous among the penetration testers and security consulting companies, have following four key phases, which are common among them
Information Gathering with Kali Linux
With Kali Linux you can easily perform all of these above highlighted phases. Before we explore more on information gathering with Kali Linux let me quickly cover active and passive types of info gathering.
Passive Information Gathering is something where you do not directly interact with the targeted system and this is usually gathering information from sources like search engines. Beneficial where you don’t want to alert the target side.
Active Information Gathering is the first step where you interact with target to gather information and this is the live method. This is more accurate but generate alerts at the target side.
As I mentioned that in active information gathering you interact with target hence you need tools for doing this for you. Now lets have look what Kali Linux have for performing active information gathering.
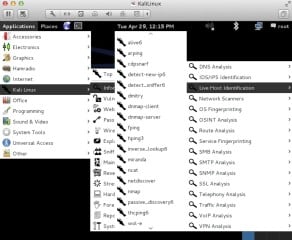
Figure 7. The above figure highlights the tools Kali Linux provides you for performing active information gathering. Ranging from protocol and DNS analysis, network scanning & operating system figure printing, what else you want?
Scanning the target with Kali Linux
At this stage of penetration testing, security experts need to scan the targets. Before you start hitting the target its better to check if the target is up and running.
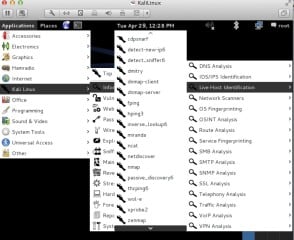
Figure 8. Kali Linux provides bunch of tools to scan the target for live systems and then fingerprint them easily. Below figure highlights the list of tools, which can be used in these steps
Vulnerability Analysis with Kali Linux
When security experts talk about vulnerability analysis, the most famous security product which almost all security experts use for vulnerability scanning is Nessus and unfortunately its not free for life therefore Kali Linux doesn’t include this tool by default.
However you get access to other vulnerability scanners with Kali Linux. You get handfuls of vulnerability scanning tools ranging from nmap, database vulnerability analysis, cisco platform, fuzzing tools and other miscellaneous scanners, which helps in achieving the successful vulnerability assessment.
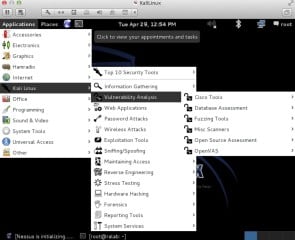
Figure 9. Vulnerability Analysis with Kali Linux
Installing Nessus on Kali Linux
Hey! As I already mentioned that almost all security experts use Nessus so I will not let you go without testing the Nessus flavor on Kali Linux. Lets quickly see how you can install Nessus on Kali in quick steps.
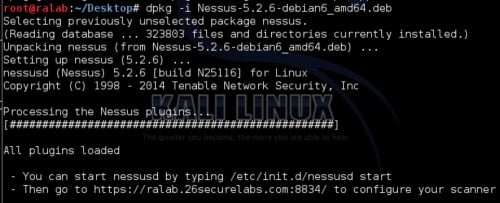
Figure 10. Download the latest Nessus Debian package from Tenable website. And as shown in the below figure install it through command line
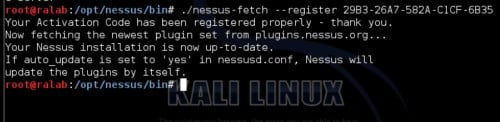
Figure 11. Next, you should have the Nessus registration key from tenable, which is easy to receive with home feed license. Now register your installation with tenable as shown in below figure
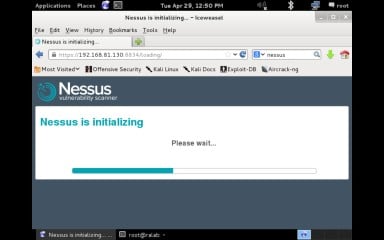
Figure 12. Now restart Nessus and access the your fresh installation of Nessus through the web interface
If everything goes well you should see the next screen to create your Nessus userID and password.
Hurrah – all working fine. Lets move to the final phase of the penetration testing part, which are the last and the interesting bit in interacting and testing your target.
Exploiting with Kali Linux
Metasploit the great penetration-testing framework that is widely used by penetration testers and security experts across the globe comes pre-installed with Kali Linux. However there is slight tuning, which is required before you start using it in your lab environment.
Starting Metasploit framework
In keeping with the Kali Linux policy, there are no network services, including database services, running on boot so there are a couple of steps that need to be taken in order to get your Metasploit framework to up and running with database support.
Start postgresql service by issuing command as follows:
root@ralab:# service postgresql start
With PostgreSQL up and running, we next need to launch the Metasploit service. The first time the service is launched, it will create msf3 database user and a database called msf3. The service will also launch the Metasploit RPC and Web servers it requires.
root@ralab:# service metasploit start
Now that the PostgreSQL an Metasploit services are running, you can launch
msfconsole and verify database connectivity with the db_status command.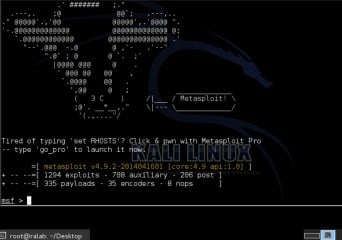
Figure 13. Here you go with the most popular exploitation framework for exploitation vulnerabilities with in your Kali Linux lab environment
Conclusion
This is a quick and detailed guide on how to perform penetration testing with Kali Linux and adding the world-class vulnerability scanner Nessus that doesn’t come by default with Kali Linux. What I have presented is just the beginning of exploring this world-class security distribution, which is widely used across the globe by information security experts.
Keep reading and exploring Kali Linux. Come back soon for more fun and learning!
Sign up here with your email